States prepare for massive winter storm
FOX Weather meteorologist Bayne Froney joins ‘America’s Newsroom’ in Dallas, Texas as the first signs of a massive winter storm begin to show. Texas is preparing accordingly following the devastating winter storm five years ago.
NEWYou can now listen to Fox News articles!
Weather forecasters are warning that a major winter storm is expected to impact large portions of the United States starting Friday. Forecasts call for snow, freezing rain and ice stretching from Texas and the Southern Plains through the Southeast, Mid-Atlantic and into the Northeast. This system is concerning because it combines ice accumulation, gusty winds and plunging temperatures. In many regions, especially across the South and parts of the Mid-Atlantic, infrastructure is not designed to handle prolonged ice events.
That increases the risk of extended power outages and disrupted cell service. When the grid goes down, everyday tech becomes critical. Phones, alerts, vehicles and apps may be your only connection to updates and emergency help. Preparing now matters far more than reacting later.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide – free when you join my CYBERGUY.COM newsletter.
RUSSIAN WINTER STRIKE LEAVES NEARLY 800K HOMES WITHOUT POWER AND HEAT IN UKRAINE’S DNIPRO REGION
Ice storms can take down power lines fast, leaving homes without electricity and cell service for hours or even days. (AP Photo/Charles Krupa)
Why ice storms are especially disruptive
Ice storms cause more damage than most people expect. Unlike snow, ice sticks to everything and adds significant weight. Ice builds up on trees and power lines, causing branches to snap and lines to fall. Utility crews often cannot begin repairs until conditions improve, which delays restoration. Forecasters at Fox Weather warn that freezing rain across the South and interior Southeast could be particularly damaging, while snow and wind farther north may slow emergency response.
Even if cell towers remain standing, networks often overload during severe weather. When thousands of people try to call at once, connections fail. Texts and alerts usually have a better chance of getting through. That is why you should assume you may be offline longer than expected.
Immediate tech actions to take before the storm hits
These steps are simple, but timing matters. Do them before the weather conditions worsen.
Charge devices and prepare backup power
- Charge all phones, laptops, tablets and battery packs
- Fully charge wearable devices like smartwatches
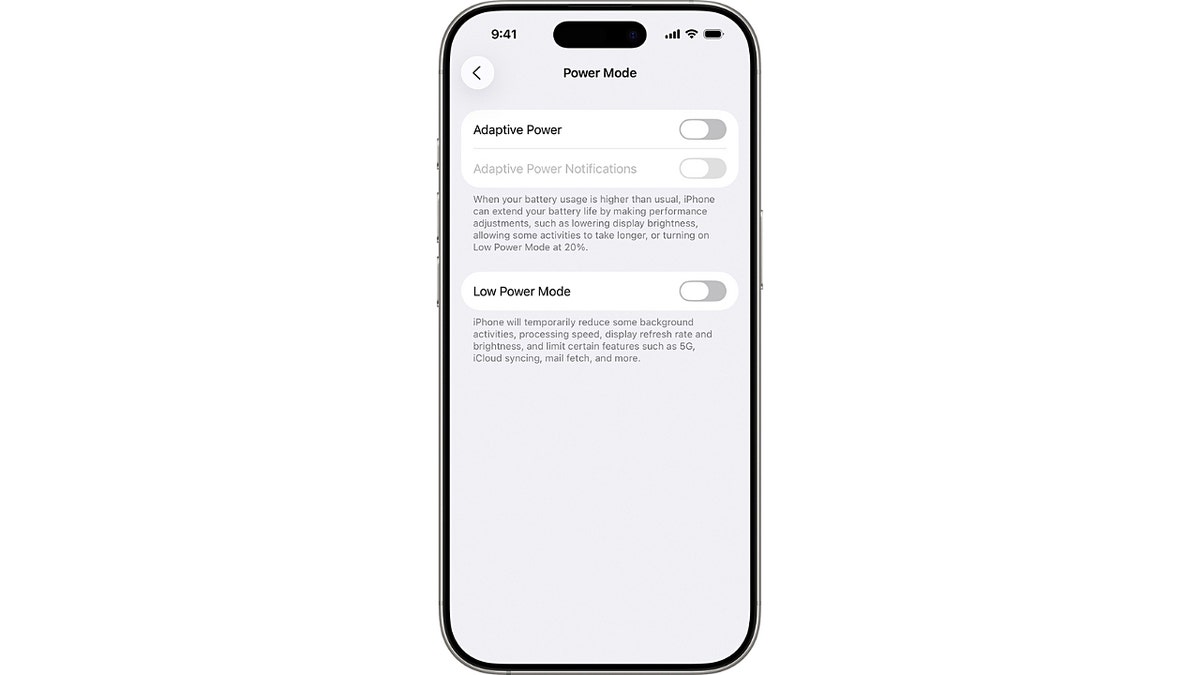
- Turn on Low Power Mode on phones now
- Lower screen brightness to extend battery life, and check out these other tips to keep your phone battery charged longer
- Make sure you have a reliable portable charger on hand, like those highlighted in our 5 best portable chargers for emergencies on Cyberguy.com.
- For outages that could last days in this winter storm, a good generator can keep your home powered the longest and safest.
- Reliable lighting matters during storms and blackouts. Invest in a high-output flashlight and hats with built-in lights that can be especially useful when visibility is poor.
- Keep a battery-powered weather radio on hand so you can receive emergency updates even if power and cell service go out.
A fully charged phone, smart power settings and a reliable portable charger can keep you connected early in an outage while longer-term home power solutions carry you through the days ahead.

A woman walks with an umbrella in the rain in the Manhattan borough of New York, Feb. 5, 2014. (REUTERS/Carlo Allegri)
Plan for offline communication and limited cell service
- Download offline maps for your area
- Save emergency contacts locally on your device
- Write down key phone numbers on paper
- Plan to text instead of calling if networks are congested. Text messages use less bandwidth and often go through when calls fail.
- Cold weather can also make phones harder to use. Touchscreen-compatible winter gloves let you stay connected without exposing your hands to the cold.
Set up a family check-in plan before the storm
- Agree on specific check-in times
- Choose one out-of-area contact everyone can message
- Avoid constant calling, which can overload networks
Clear expectations reduce panic and unnecessary phone use.
Make sure emergency alerts are enabled
Emergency alerts can reach your phone even when apps and social media cannot. They are designed to cut through network congestion and deliver critical warnings.
How to turn on emergency alerts on iPhone
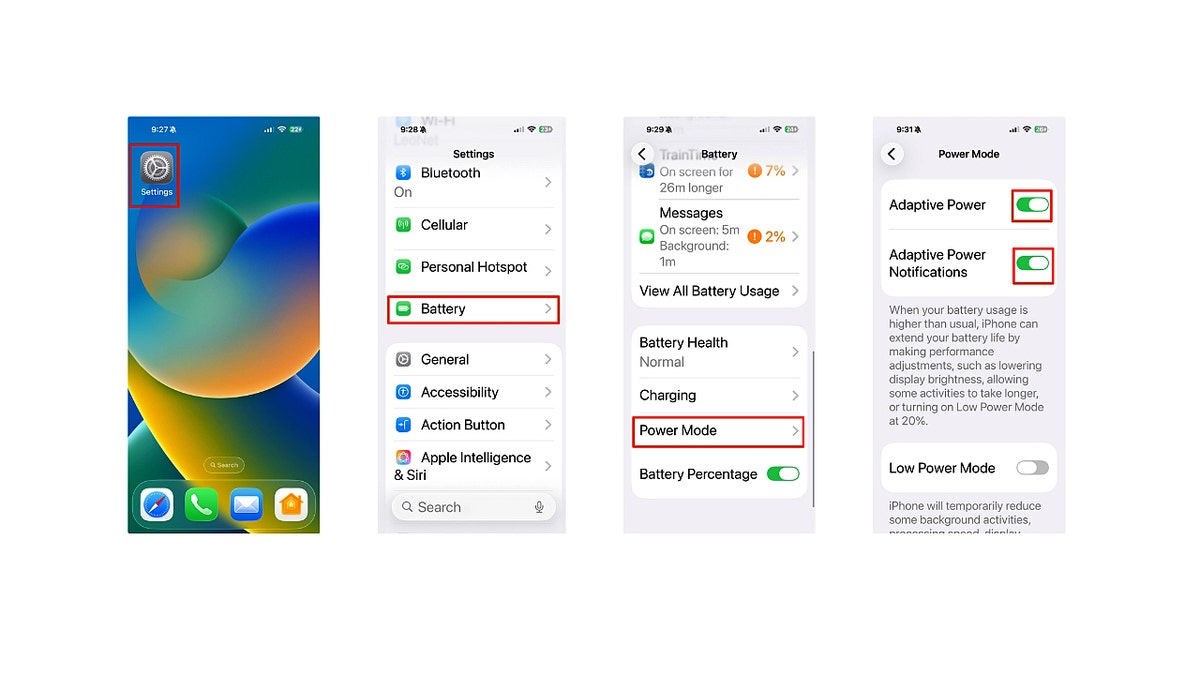
- Open Settings
- Tap Notifications
- Scroll to Government Alerts
- Turn on Emergency Alerts
- Enable Always Play Sound
- Turn on Imminent Threat Alerts under Enhanced Safety Alerts
US POWER CRUNCH LOOMS AS OKLO CEO SAYS GRID CAN’T KEEP UP WITHOUT NEW INVESTMENT

Ice storms add heavy weight to trees and power lines, causing widespread damage and outages that can overwhelm repair crews and communication networks for longer than expected. (AP/Craig Ruttle)
How to turn on emergency alerts on Android
Settings may vary depending on your Android phone’s manufacturer
- Open Settings
- Tap Safety and emergency or Notifications
- Select Wireless emergency alerts
- Turn on Severe threats and Extreme threats
- Enable Allow alerts and Alert sound
On some phones, you may also see options for Public safety messages or Emergency alerts, which should be turned on. These alerts may include evacuation notices, shelter updates and severe weather warnings.
Both iPhone and Android let you preview alert sounds and settings in these menus, so take a moment to test them now and make sure alerts are loud enough before severe weather hits.
Know how to use Emergency SOS on your phone
If you need help during a winter storm, Emergency SOS can contact emergency services even when you cannot unlock your phone or make a normal call. Set this up now. Do not wait until you are stressed, cold or without power.
How to set up and use Emergency SOS on iPhone
- Open Settings
- Tap Emergency SOS
- Turn on Call with Hold and Release or Call with 5 Button Presses
- Scroll down and add emergency contacts
To activate Emergency SOS during an emergency, press and hold the side button and a volume button, or quickly press the side button five times, depending on your settings.
How to set up and use Emergency SOS on Android
Settings may vary depending on your Android phone’s manufacturer
- Open Settings
- Tap Safety and emergency or Privacy and safety
- Select Emergency SOS
- Turn on Use Emergency SOS
- Choose how SOS is triggered, such as Require to swipe to call
- Add emergency contacts and medical information by clicking Emergency sharing settings
On many Android phones, pressing the power button five times will trigger Emergency SOS. Emergency SOS can call for help, share your location and alert emergency contacts when conditions are dangerous.
If cell towers go down during this storm, features like Emergency SOS can still help you reach emergency services. Our guide explains in more detail how these lifesaving settings work.
Apps you should have installed ahead of time
The right apps can deliver critical updates when power is out, cell networks are strained and social media is unreliable. Install and set these up before the storm arrives.
Weather and severe alert apps
- Fox Weather app: A trusted option for real-time forecasts, winter storm alerts, radar tracking and location-based notifications. Make sure local alerts are turned on.
- MyRadar Weather Radar: A highly rated radar app that shows storm movement in real time and sends push alerts when severe weather is approaching your area.
- Storm Shield Severe Weather App: Delivers National Weather Service alerts based on your exact location, similar to NOAA weather radio warnings, with clear push notifications for winter storms and ice events.
- NOAA Weather Radio apps (iPhone and Android): These apps stream official NOAA Weather Radio broadcasts, providing continuous updates, watches and warnings directly from the National Weather Service. Weather radio streams often remain available even during major outages.
Using more than one weather app can give you redundancy if one service is delayed or overloaded.
Utility and outage tracking apps
- Your local power utility app: Most utilities offer apps that allow you to report outages, view outage maps and track restoration progress in real time.
- FEMA App: Provides official weather alerts, disaster resources, shelter locations and safety guidance during severe weather events.
These apps can confirm outages, provide restoration updates and reduce unnecessary calls to utilities when systems are overwhelmed.
Do not overlook vehicle tech and preparedness
Your vehicle may become a critical resource during extended outages.
Prep your car before conditions worsen
- Fill your gas tank early. A full tank allows you to run the engine briefly for heat or charging if needed.
- Keep a phone charger in the car.
- Store a fully charged portable power bank in the glove box or center console. This gives you emergency phone power if your car battery dies or you cannot run the engine.
- Download weather and road condition alerts.
- Also, consider buying a Snow brush and ice scraper, jumper cables, a set of 6 LED Road Flares Emergency Lights and a First Aid Trauma Pack with QuikCloth, so you are not caught off guard in an emergency.
- There are also portable tech solutions designed to help you stay warm and powered during outages or roadside delays, including heated gear worth purchasing in advance.
Storms also bring scams and fraud attempts
Severe weather creates ideal conditions for scams. Power outages, delayed responses and anxiety make people more likely to trust messages that appear urgent or official.
Fake utility and restoration scams
Scammers often impersonate electric, gas or water utilities.
- Texts or calls claiming your power will be restored faster if you pay
- Messages warning service will be shut off unless you act immediately
- Spoofed phone numbers that look like your local utility
What to know: Utilities do not charge fees to restore power and do not demand payment by text, gift cards or apps.
Emergency aid and disaster relief scams
These scams spike right after storms hit.
- Messages promising emergency funds, fuel vouchers or hotel assistance
- Fake charity links claiming to help storm victims
- Social media posts asking for donations using stolen images
What to know: Legitimate aid is announced through official government or well-known nonprofit channels, not unsolicited messages.
Fake delivery, fuel and repair service scams
Storms disrupt normal services, which scammers exploit.
- Links claiming fuel delivery is available in your area
- Messages about delayed packages that require confirmation
- Ads for emergency home repairs that ask for upfront payment
What to know: Do not click links or pay deposits without verifying the company independently.

Charging your devices and lining up backup power now can make the difference between staying informed during an outage and being cut off once the storm hits. (Kurt “CyberGuy” Knutsson)
Account takeover and identity theft attempts
Storm chaos makes it easier for attackers to slip through unnoticed.
- Password reset emails pretending to be from banks or retailers
- Login alerts asking you to “secure” your account immediately
- Calls claiming suspicious activity that push you to share codes
What to know: Never share one-time codes or login details, even if the message looks legitimate.
How to protect yourself before and during the storm
Taking a few precautions now can help you avoid costly mistakes when outages, delays, and scam messages start piling up.
1) Slow down and verify every urgent message
Scammers rely on panic. If a message pressures you to act fast, stop and verify it through a trusted source.
2) Avoid clicking links in unsolicited messages and use strong antivirus software
Go directly to official websites or apps instead of tapping links in texts or emails. Keep your operating system up to date and use strong antivirus software to block malicious links and fake websites.
The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have strong antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe.
Get my picks for the best 2026 antivirus protection winners for your Windows, Mac, Android and iOS devices at Cyberguy.com.
3) Lock down accounts before outages hit
Enable two-factor authentication (2FA) on email, banking, and utility accounts so stolen passwords cannot be used alone.
4) Reduce your exposure with a data removal service
Many storm scams work because criminals already have your phone number, address or email. Using a data removal service to opt out of data broker sites can reduce how easily scammers target you during emergencies.
While no service can guarantee the complete removal of your data from the internet, a data removal service is really a smart choice. They aren’t cheap, and neither is your privacy. These services do all the work for you by actively monitoring and systematically erasing your personal information from hundreds of websites. It’s what gives me peace of mind and has proven to be the most effective way to erase your personal data from the internet. By limiting the information available, you reduce the risk of scammers cross-referencing data from breaches with information they might find on the dark web, making it harder for them to target you.
Check out my top picks for data removal services and get a free scan to find out if your personal information is already out on the web by visiting Cyberguy.com.
Get a free scan to find out if your personal information is already out on the web: Cyberguy.com.
5) Never pay to restore power or receive aid
Utilities and government agencies do not charge fees to restore service or release emergency assistance.
When power and internet access are limited, it is harder to verify messages quickly. That makes preparation just as important as awareness. A little skepticism now can prevent financial loss and identity theft when help is hardest to reach.
Take my quiz: How safe is your online security?
Think your devices and data are truly protected? Take this quick quiz to see where your digital habits stand. From passwords to Wi-Fi settings, you’ll get a personalized breakdown of what you’re doing right and what needs improvement. Take my Quiz here: Cyberguy.com.
Kurt’s key takeaways
Winter storms can turn small tech decisions into critical ones. Ice, power outages and overloaded cell networks can leave people cut off faster than expected, especially in regions not built for prolonged winter weather. Preparing your devices, alerts, vehicles and accounts ahead of time gives you more control when conditions worsen. It also reduces panic and limits your exposure to scams that thrive during emergencies. A little planning now can make a big difference when help is harder to reach.
Have you taken steps to prepare your tech for this winter storm, or did this checklist highlight something you still need to do? Let us know by writing to us at Cyberguy.com.
CLICK HERE TO DOWNLOAD THE FOX NEWS APP
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide – free when you join my CYBERGUY.COM newsletter.
Copyright 2026 CyberGuy.com. All rights reserved.